MEO Encryption Download. MEO is a data encryption application to encrypt or decrypt files of any type, including Microsoft Word, Excel and PDF documents. MEO allows you to protect your sensitive data against un-authorized viewers by utilizing the latest data encryption. The statement 'Even encryption software like PGP/GPG stores the keys in a file' is misleading. PGP encrypts those keys using a passphrase known only to the user. PGP also uses secure memory for keys ensuring that they are never cached to the HD and PGP goes through great lengths to make it difficult to find a key using memory inspection. Microsoft Office 2010 Serial Key For Windows7 Avast Premium 2015 Serial Key Iobit Driver Booster Pro 5.5 Serial Key Meo Encryption Free Serial Key Game Of Thrones Telltale Serial Key C & C First Decade Serial Key Aurora Hdr 2018 Serial Key Advanced Systemcare 10 Rc Pro Serial Key How To Use Windows Serial Key. MEO Encryption Download. MEO is a data encryption application to encrypt or decrypt files of any type, including Microsoft Word, Excel and PDF documents. MEO allows you to protect your sensitive data against un-authorized viewers by utilizing the latest data encryption technologies.
Encrypt and decrypt files and keep your data secureMEO is easy file encryption software for Mac or Windows that will encrypt or decrypt files of any type. Protect sensitive data against unauthorized viewers with the latest data encryption technologies to keep your important documents safe and secure.
You can easily send encrypted emails, or create self-extracting encrypted files so the receiver can open the encrypted files on any Windows or Mac computer without needing to install the encryption software on their machine. Get it Free. A free version is available for non-commercial use. If you will be using MEO encryption software at home you can download the free version here. | Download NowBuy Online |
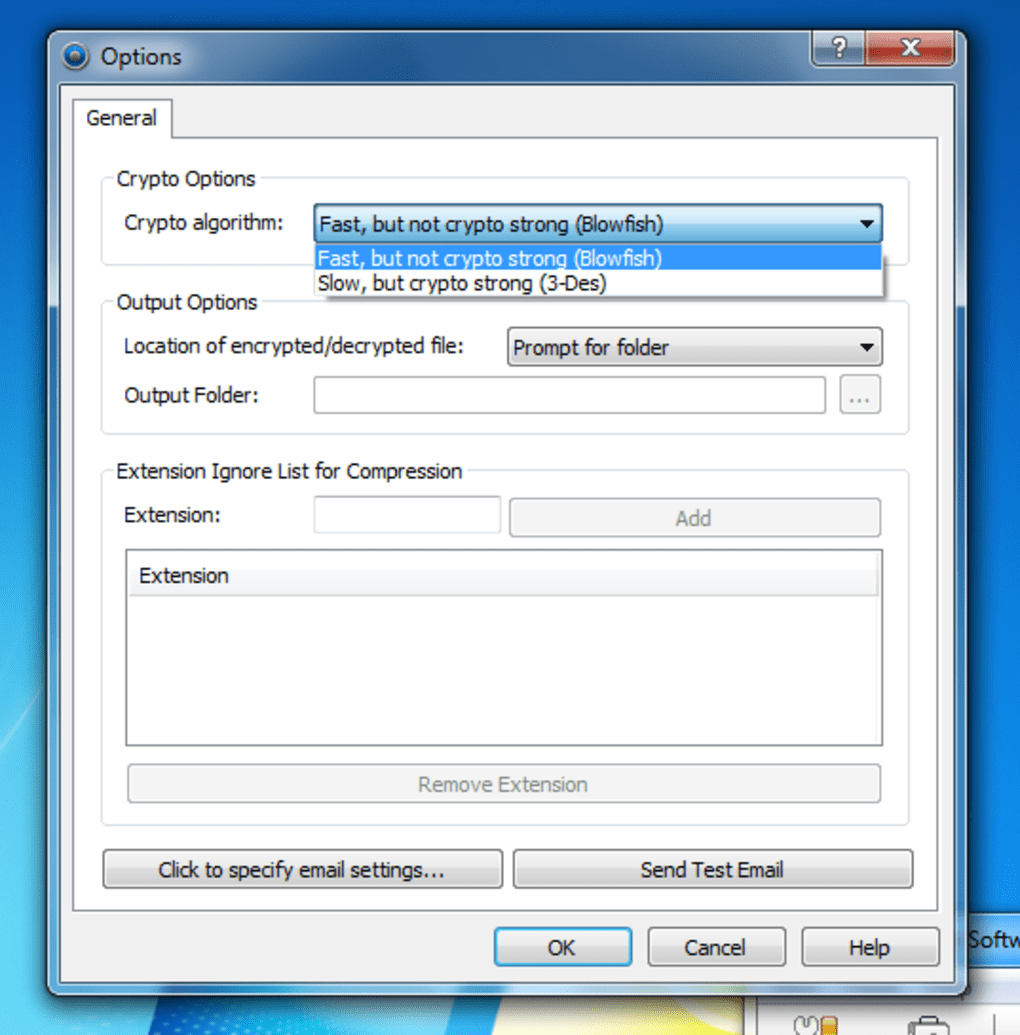
Encryption Features
|
Encrypt Features
System Requirements
Download Now
- for Windows
- for Mac OS X
Screenshots
Questions (FAQs)

 Technical Support
Technical SupportPricing & Purchase
Related Software
Data Recovery
Data DVD/CD Burner
CD Ripper Software
Invoicing Software
Accounting Software
Inventory Software
Meo File Encryption
More Software...More Business Software...
What does the protection process look like?
Meo Encryption Free
The protection process is fully automated (it can be run from the command line) and consists of rebuilding, modification and encryption of the compiled software, its code, data structures, and adding additional code which manages the protection.
Application and protection code integration example
Free Encryption Software

Meo Encryption Software Review
Below you can find sample usage of the basic encryption macros from the licensing system. Code between the two markers is encrypted during the protection process, and after the application is launched, the code is decrypted and executed only if a valid license key is found. The license key contains the decryption keys, so decryption is impossible without it. After the code is executed it gets re-encrypted.
- C / C++
- Delphi / Pascal
- D
- PowerBASIC
- PureBasic
Protected & unprotected application differences
After protection, the application code is modified to protect it from reverse engineering analysis and attempts to recover its original form, which would make it possible to analyze or modify its code and data. Code, data and additional application resources are encrypted using strong cryptographic algorithms and multilayer polymorphic encryption. The protection code itself is transformed into a highly secure form using innovative metamorphic engine. It makes the analysis of the entire protection an extremely technically difficult and time consuming task, even for reverse engineering professionals.
It's worth mentioning that after the protection, the application code is strictly integrated with the protection code; if an attacker tries to remove the protection code, the application itself will remain safe and it will be impossible to run and use it.
